Updated: May 2023
Counterfeit devices: an enterprise cyber-security threat
Bring Your Own Device (BYOD) policies are becoming more prevalent as remote working and connecting ‘on-the-go’ are now commonplace for employees. However, keeping track of the various devices connecting to an Enterprise’s IT network can be difficult, as well as ensuring that those devices match the owner and are authentic. Any vulnerability opens up the potential for a major breach in security.
Counterfeit devices pose a significant threat to enterprise networks and that trend is only increasing. These devices are becoming more sophisticated, difficult to spot, and easy to obtain. A counterfeit phone is almost indistinguishable from its authentic counterpart. They are also easy to buy and may even be sold on seemingly trusted eCommerce websites and delivered by reputable shipping companies. Most worryingly, they are also becoming more dangerous and resulting in more damage.
A recent experiment carried out by the DeviceAssure team demonstrated just how dangerous these counterfeit phones can be. Not only was the counterfeit iPhone in question inauthentic, it also tried to download and execute malicious code on the company's internal network. A similar investigation by Trail of Bits into two counterfeit smartphones found malware, rootkits, unpatched vulnerabilities and insecure bloatware. Each of these pose a serious threat to unsuspecting enterprises.
Many enterprises use Mobile Device Management (MDM) or Enterprise Mobility Management (EMM) solutions to manage their fleets of mobile devices, while some employ a Managed Security Service Provider (MMSP). However, these solutions won't be effective if they're exposed to counterfeit devices. As unbelievable as it may sound, it's actually naive to assume and trust that a device is exactly what it says it is.
Unfortunately, in 2021 alone, EU authorities seized 66 million counterfeit devices. Similarly, any enterprise which adopts a BYOD (bring your own device) policy is very much at risk from unknown and potentially harmful devices connecting to internal WiFi networks. Sourcing a top of the line smartphone for 10% of the true cost may be attractive for an employee, but for the enterprise it's a high price to pay if security systems are compromised. Mobile phones are also known to be one of the most common devices associated with security breaches in recent years.
What can be done?
Verifying the authenticity of any devices connecting to a business network is a good first step in controlling cyber-security risks. If a device really is what it claims to be, the chance of any security issues and data leaks are significantly reduced. Enterprises have a duty to themselves to protect against the dangers of non-authentic devices. DeviceAssure equips enterprises with the information to make smart decisions about the provenance of devices by protecting them from the threat posed by fraudulent or misrepresented devices and user-agents.
Here's an example of how DeviceAtlas currently implements this on its internal network:
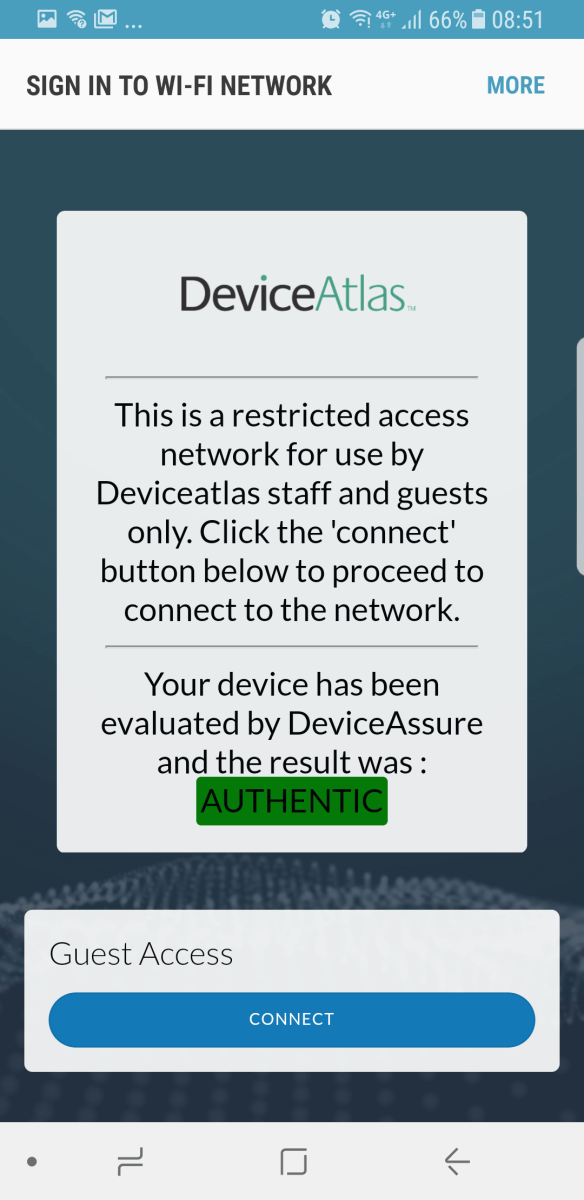
Not every device is what it seems, don’t blindly trust them – verify first.



