
We've undoubtedly been living in a digital world for some time now. According to DeviceAtlas's data, there are currently >85,000 connected device models globally, of which more than 70% are mobile phones specifically. With an increasing reliance on mobile devices to carry out day to day tasks, knowing as much about these devices as possible is critical. It also requires more robust cyber security measures to ensure that online user accounts and profiles are protected. This is particularly critical considering that phishing attacks increased by 61% in 2022 with credential harvesting being the number one cause of breaches. Over a third of these threats were also hosted on trusted services such as Google, Microsoft and AWS, making these attacks appear sophisticated and legitimate to unsuspecting users.
Did You Just Log In?
This increase in cyber security attacks has resulted in businesses implementing more sophisticated security measures for users, particularly with regards to account accessibility. Login processes now often involve two-factor-authentication (2fa), adding an extra layer of security for the user and protecting their account against potential cyber-attacks. An additional security measure which many businesses also implement is to send the user an email if their account has been accessed by a different device than what was used to access it previously. For example, if a user logs into their account using the phone’s internet browser rather than via the app itself, this may trigger an email to the user informing them that their account has been accessed by a different device and to change their password if they believe that the login attempt looks suspicious. Similarly, many apps which contain more sensitive information such as banking details, medical history, etc. require 2nd factor authentication from users if they attempt to log in from a desktop device. This will usually involve the user having to verify the login using the mobile app.
The purpose of these device login emails is to provide reassurance for users and protection against security threats. Unfortunately, despite being such a critical part of security efforts, many of these emails unfortunately lack the very information that the user needs to be aware of in order to decide if something bad has happened - details about the device that is accessing the account.
Below are some examples of device login emails from well-known, global brands from a variety of industries following login attempts from different devices. Needless to say, the information contained in these emails about the devices in question are scant at best. Also notice that one email doesn’t actually contain any device information, just the location and time of access.
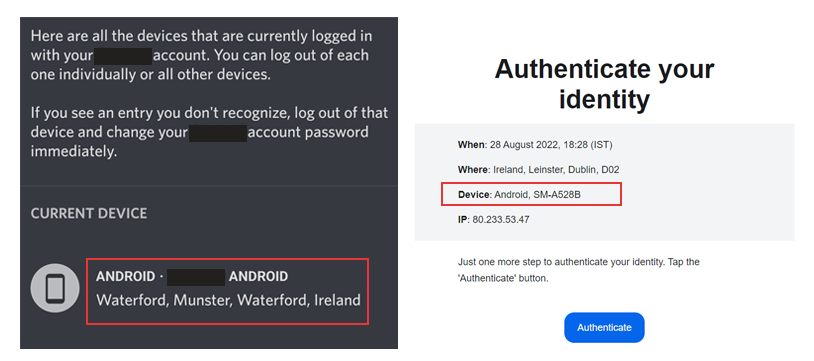
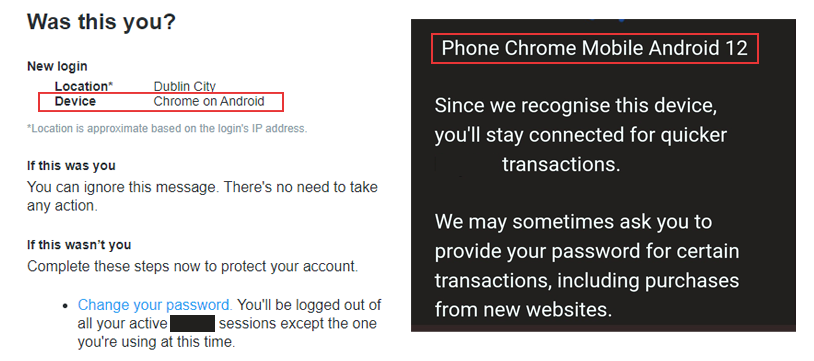
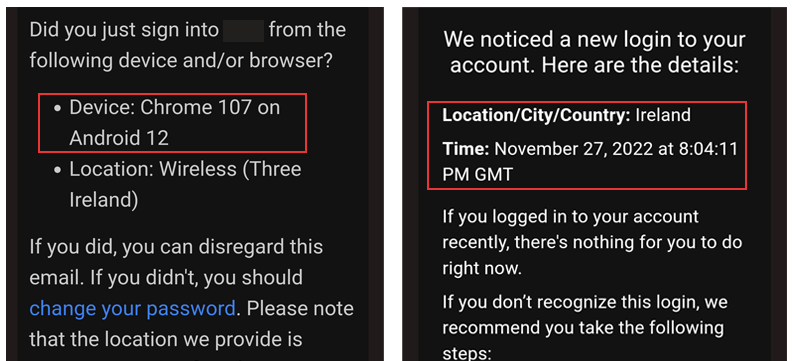
Mass Confusion
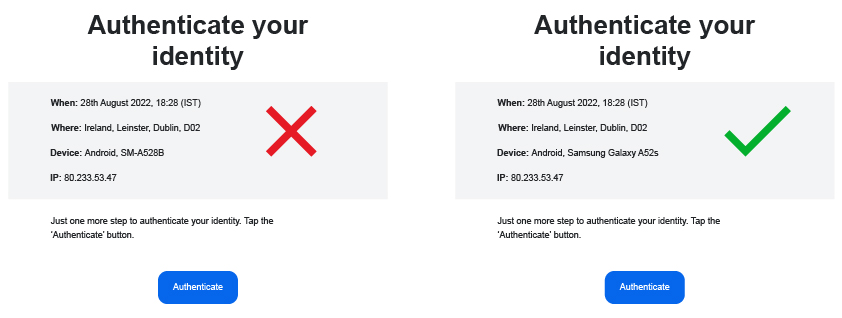
Labeling this a significant problem seems mild, it’s far more problematic. There is no helpful information about the devices mentioned in these emails, and in some cases they aren't even devices! OS Browser and Version are merely related to the software system, not the physical device itself. In one case we can even see Phone Chrome Mobile Android 12 which is plainly bizarre. The most elaborate description appears to be Android, SM-A528B; those familiar with internal device naming conventions know that this would be a Samsung Galaxy A52S, SM-A528B being the internal model name allocated by the manufacturer. Unfortunately, very few consumers are privy to this information and such a string of numbers and letters will mean nothing to them.Even more worrying is the possibility that this could be perceived as a nefarious email intended to hack into the user's account; as phones are becoming increasingly relied upon as a second factor of authenticity, the impact of security breaches is greater. So, in a tragic twist of irony, the very thing that major companies are trying to protect users from may be causing serious concerns. This is especially true when we consider the sophistication of cyber-attacks. CTO of DeviceAtlas, Ronan Cremin, says: "When you are being asked to verify that a login is correct, it's doubly disturbing if the device they say you're logging in on is unrecognizable to you. They're asking you to verify something that no normal person is empowered to comprehend. Seeing a random string of digits could understandably look like a hack to someone."
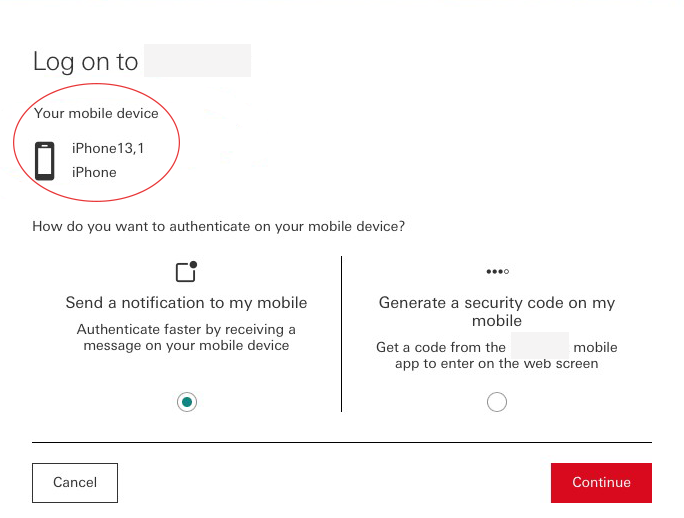
We have seen many poor implementations of 2FA involving mobile devices also. Quite often a website login will ask a user to provide a second factor authentication by performing an action on the mobile app associated with the service. Unhelpfully, as is the case with the did-you-just-log-in? emails mentioned above, services will often refer to the device in question using cryptic internal model names that, at best, means nothing to most users but can often be actively misleading. Consider the screenshot below. This is a very well-known international bank prompting a user to verify a web login using an app on their iPhone 13,1. A user might assume that this means iPhone 13 but in fact this is Apple's internal model name for the iPhone 12 mini. The bank in question has simply assumed that the phone's internal model name will make sense to users and surfaces it verbatim. So, rather than providing helpful information the bank is actively misleading the user by not taking the time to use consumer-friendly device marketing names for registered devices.
Best Practice for Device Login Emails
It's frightful to think that the above screenshots are just some of the many examples of major companies sending vague and confusing device verification emails to their user base, yet there is a fix which is so simple, a solved problem: a device detection solution. Best practice would be for a device login email to contain recognizable information pertaining to the device in question, leaving no ambiguity for the user. For mobile device verification in particular, instead of just querying what model the phone is with 2fa, adopting a device detection solution to interpret it will offer far more reassurance, including the consumer marketing name which the user will recognize (in this case the Samsung Galaxy A52S). Being able to confidently rely on such a solution is especially important in a world where mobile devices are an integral part of many services. Not knowing the user's device is not good enough anymore. Businesses must know which devices their users are using to access content with and be able to describe them in a way that makes sense to those users.
Below is an example of one device login email without a device detection solution and one with. Such a simple, yet critical change can make a huge difference:
Commercial Benefit
While arguably mission critical to a company's brand, utilizing accurate and recognizable device information for login verification emails may also have a commercial benefit to some businesses. For example, digital content services are among many businesses that send out new device emails when a user logs in on a different device. These content providers are also currently experiencing significant issues surrounding password sharing, so from a subscription management perspective, being able to accurately name the specific device that a user logs in with each time may draw attention to the possibility of password sharing if these devices in question are invariably different each time. This may also provide an opportunity for increased subscription revenue if device checks are carried out on these accounts.



